Mobile app security platform – Build38
Build38: The Next Generation Mobile App Security Platform

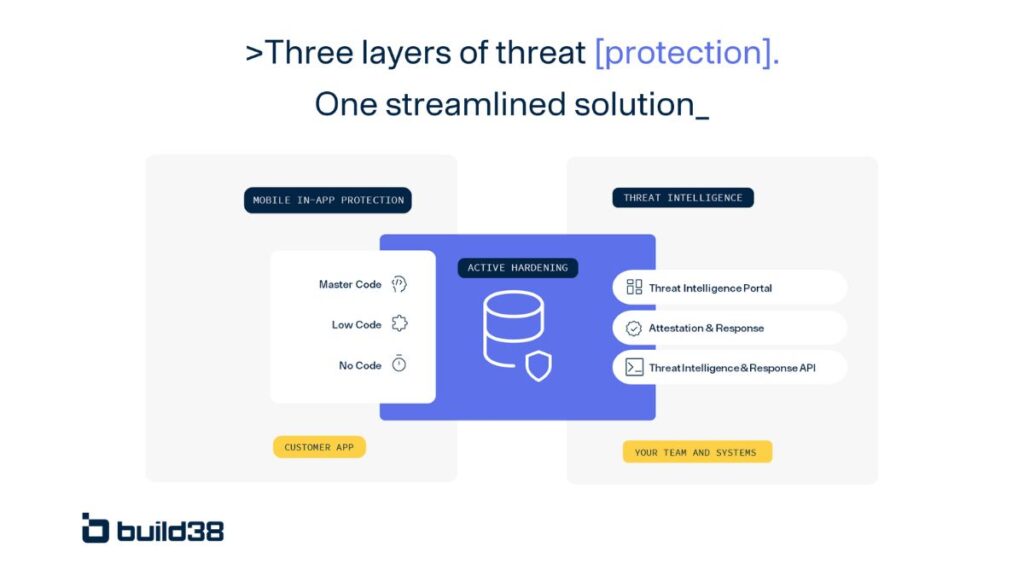
Build38: Top-tier Mobile App Protection fortified by AI-driven Active App Hardening and cloud-based Threat Intelligence
Build38 empowers businesses to effectively counter security attacks targeting their mobile apps.
Our platform streamlines compliance requirements, expedites certification processes, and eliminates the need for extensive security expertise within mobile app teams. It uniquely caters to the rigorous security requirements of various mobile applications, including mobile-first banking apps, SoftPOS apps, digital ID apps, digital wallets, crypto wallets, and many other application types.