
Press Releases
Latest news from Temenos.

GRAND-LANCY, Switzerland – DECEMBER 11, 2025 – Temenos (SIX: TEMN), a global leader in banking technology, today announced t...

GRAND-LANCY, Switzerland, December 10, 2025 – Temenos AG (SIX: TEMN), a global leader in banking technology, today announces a...

GRAND-LANCY, Switzerland – December 5, 2025 – Temenos (SIX: TEMN), a global leader in banking technology, today announced it...

GRAND-LANCY, Switzerland, December 3, 2025 – Temenos AG (SIX: TEMN), a global leader in banking technology, today announced th...

GRAND-LANCY, Switzerland – NOVEMBER 18, 2025 – Temenos (SIX: TEMN), a global leader in banking technology, today announced i...

Hanoi, Vietnam – NOVEMBER 10, 2025 – VPBank, one of Vietnam’s top five private commercial banks, has successfully moderniz...
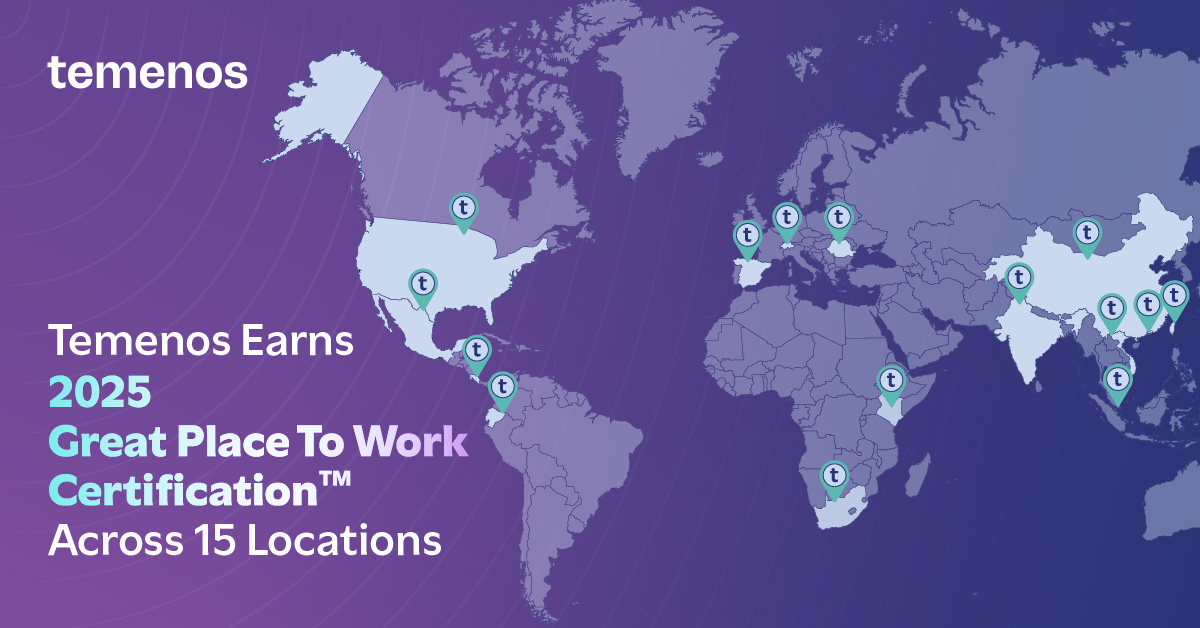
Temenos now certified in the US, India, Ecuador, Hong Kong and Taiwan in addition to 10 locations announced earlier this year.

